专业移动应用/游戏数据分析平台助力 全球增长
值得信赖的移动市场数据,发掘市场潜力,洞悉产品模式
全球 8 大平台实时监控
在线应用/游戏监控 |23:35 更新
合作客户
移动应用
游戏赋能
投资决策
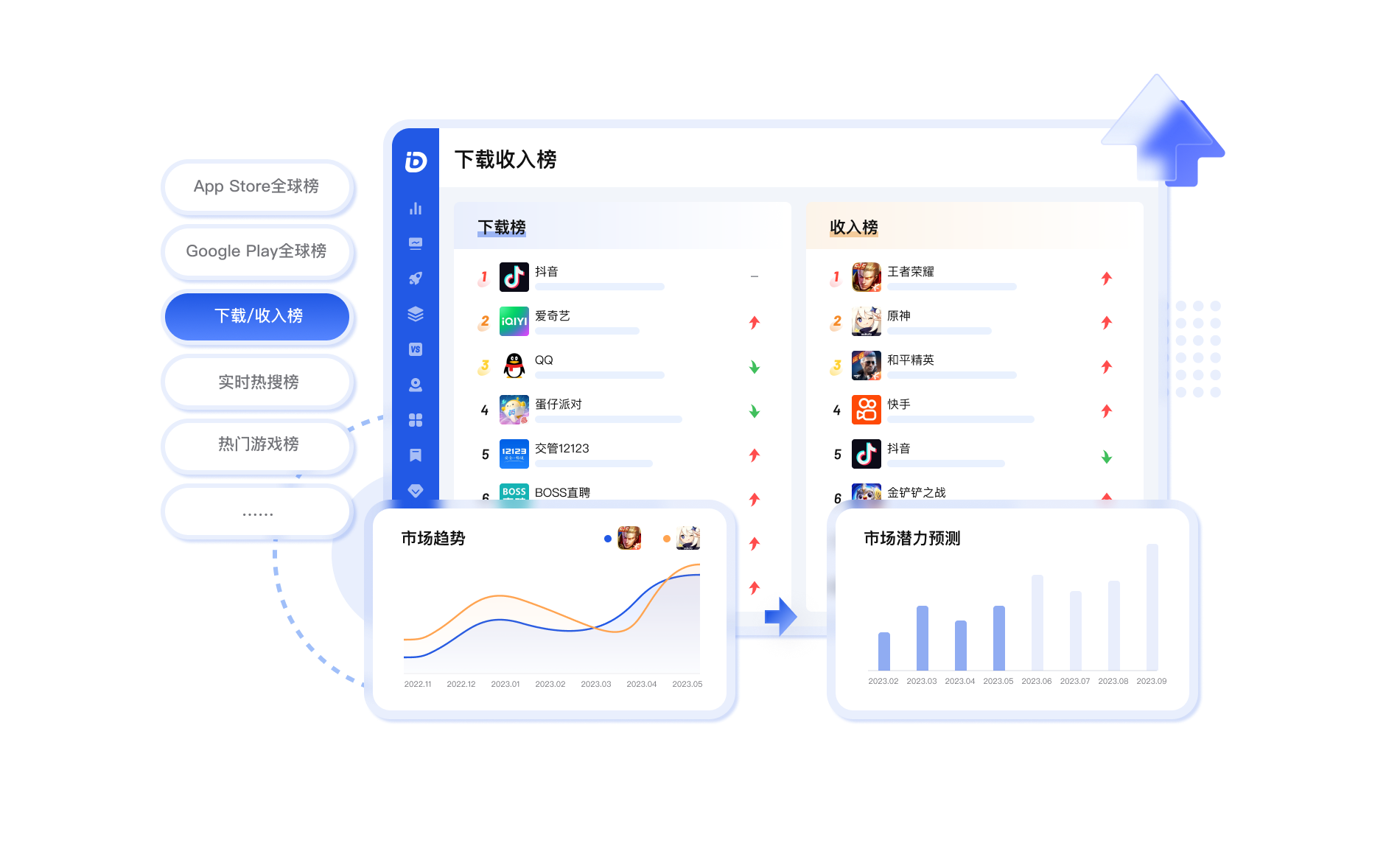
应用排行
通过不同维度排行榜更加直观了解应用现状,分析应用市场趋势,快速锁定潜力市场,抓住增长机会
市场跟踪
透过全球各大应用商店聚合数据,进行全行业规模分布和市场跟踪
全球增长
借助全球应用下载收入、用户分布趋势,精准定位全球增长趋势和市场
点点数据辅助您进行高效的数据挖掘,更快的决策制定!

全球应用/游戏数据更新
全球各大应用市场数百万款应用/游戏信息实时更新

多维度/定制化榜单
查看数百万款应用的估算数据,了解是哪个商店、哪个国家/地区、哪类应用或什么设备在推动增长。

ASO/ASA策略分析
充分了解竞品关键词策略,通过付费搜索广告提升APP下载,全方位提升产品排名,以更低成本驱动用户精准获取。

技术集成
通过分析技术集成、服务支持,深刻剖析应用辅助手段,缩小甚至超越竞品的用户体验

下载/收入
结合应用/游戏在全球不同国家/地区的预估下载收入数据,分析应用市场趋势,锁定快速增长的市场

用户粘性
通过活跃用户数、市场渗透率、使用时长和使用频率等了解用户参与度指标

用户画像&行为分析
基于用户特征和用户行为分析,辅助产品运营和品牌传播,提升应用口碑直观分析您和竞品的用户重叠情况,取长补短,吸引更多用户

竞品分析
追踪和监控竞争对手的市场占有率、增长趋势以及排名趋势
利用全面的应用市场数据不断改进您的 App 产品策略















